University of Advancing Technology Boards
Network Security
Boards Requirement 1
Create a network infrastructure design communications document that includes identified hardware components, connections to outside world, identified physical layer connectivity (media) and addressing, including operational and security components in the design.
Company Network Infrastructure
This project outlines the network infrastructure and security policies of a company with two offices located in San Diego and Phoenix. The network includes servers, VLAN segregation for added security, and VPN for secure communication and collaboration between branches. The Active Directory is used for centralized management of user accounts, workstations, servers, printers, and network shares. The company has different policies for each department, such as password requirements, workstation controls, printer defaults, and network share access. The on-site IT department in Phoenix has additional privileges to modify organizational units, users, workstations, and services. Overall, the project aims to ensure network security and ease of management.

OSI 7 Layer Model Flow Chart
The flow chart describes the communication between a user computer running Firefox and the Google.com web server. It illustrates the various layers of the OSI model, protocols, and technologies used at each layer. The chart also includes a frame header, IP header, and TCP header to illustrate the format of the data at each layer.
Boards Requirement 2
Install, configure and test security hardware and software tools with supporting documentation such as port scanners, vulnerability detection systems, intrusion detection systems, firewalls, system hardening, anti-virus tools, patch management, auditing and assessment.
Wazuh
Wazuh is an open-source security platform solution that offers host-based intrusion detection system (HIDS), endpoint detection and response (EDR), security information and event management (SIEM) solution, and security management and compliance solution. It features file integrity monitoring, log and events data collection, threat detection, regulatory compliance, multiple OS compatibility, cloud and container support, and integration with other open-source products like Elastic Stack and Kibana. Wazuh is highly customizable and easy to deploy with simple instructions to follow, quick deployment across systems, automatic enrollment, and the ability to customize group and address beforehand.
Windows 10 System Hardening
This Windows 10 hardening guide recommends changing the login password to be unique and complex, using an antivirus program like Cylance Antivirus, creating regular backups of data on an external hard drive, using a third-party DNS server like Quad9, modifying the default configurations of the Windows firewall, uninstalling unused programs, updating Windows 10 with the latest patches, disabling unnecessary Windows services that have privacy concerns, opting out of Windows 10's privacy options, disabling Cortana, and installing uBlock Origin on the browser for an additional security measure.
Boards Requirement 3
Construct, implement and document a script or a program to automate a security-related process or other tasks such as installation, administration, management, mapping resources, logon scripts, patch management, updates, auditing, analysis and assessment.
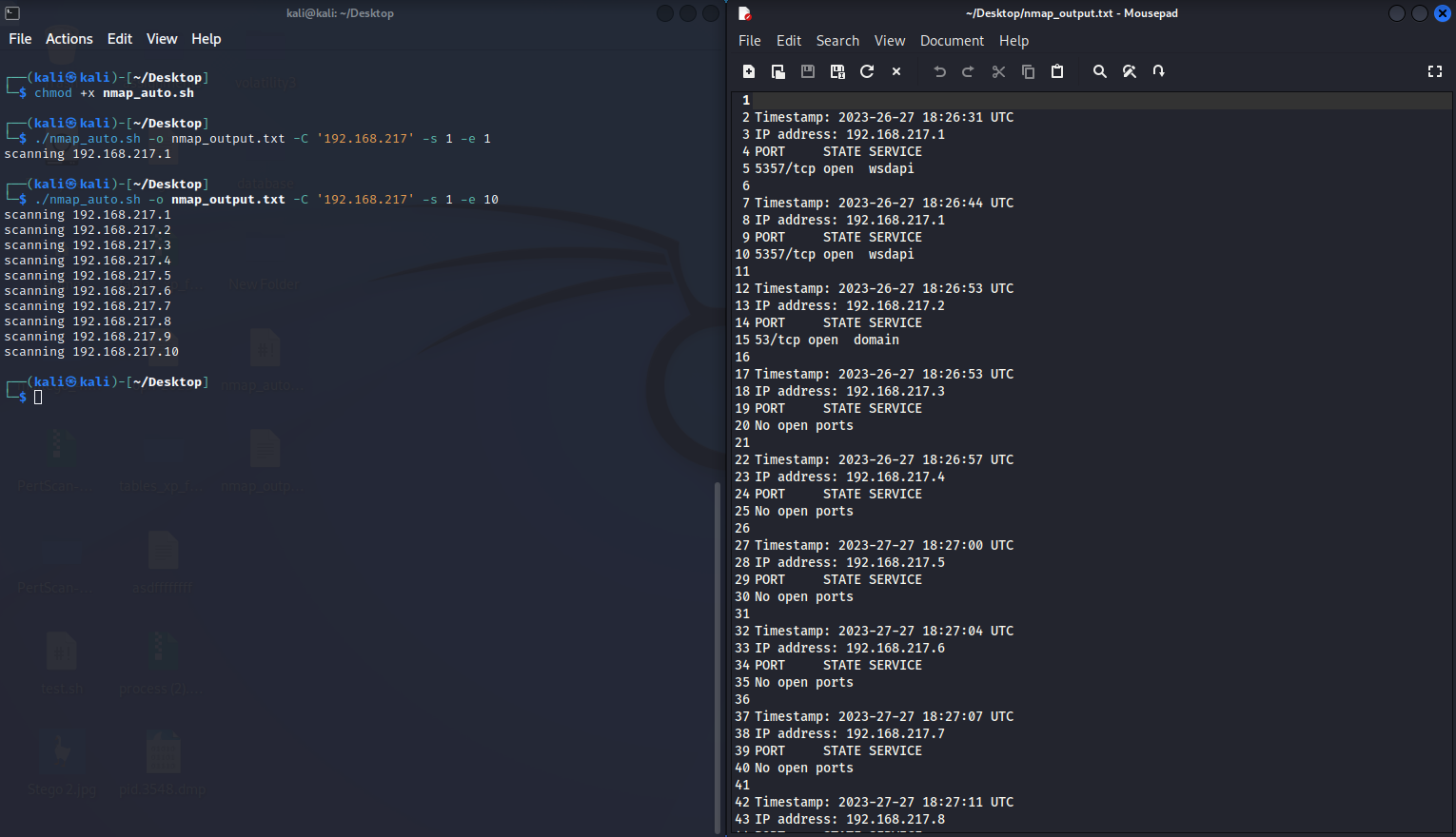
NMAP-Auto
NMAP-Auto is a bash script that takes a range of IP address octets and runs an Nmap scan on each IP address within the range, saving the results to a specified output file. It checks command-line arguments for the CIDR notation, start and end octets, and output file. The script also checks if the octets are valid numbers and if the end octet is greater than or equal to the start octet. The script uses a timestamp function and a for loop to iterate over each IP address and output the scan results to the file.
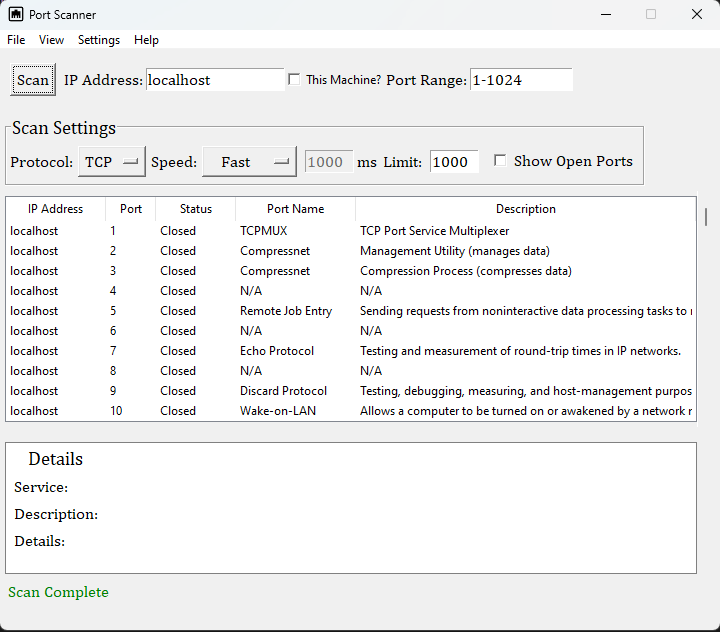
Python based Port Scanner
The application can scan a range of ports on a given IP address for open/closed statuses using TCP or UDP protocols. It has options to customize the speed of the scan and display the open ports in a table. Each port number is associated with a specific protocol and a brief description of what that protocol does. Understanding the ports and protocols used in a network can be important for network administrators, as it can help them identify potential vulnerabilities and take steps to secure their networks.
Shodan to POC
Shodan to POC is a tool that takes a search query or input file of IP addresses and runs it against Shodan. The tool parses the results to extract data such as IP address, hostname, port, and vulnerabilities. The CVEs (Common Vulnerabilities and Exposures) are identified, and the associated CVSS score and description are retrieved from Shodan's data. Shodan to POC then uses the CVE data to search for proof-of-concept (POC) exploits through various sources such as ExploitDB, Rapid7, Trickest, and InTheWild. Finally, the tool searches Nessus for viable solutions using the CVE data.
Secure Data Storage
The React app is a comprehensive password manager, password generator, and notes storage system that utilizes a Firebase database with AES encryption. The app allows users to generate strong, unique passwords, store them in the encrypted database, and organize them by category. Users can also create notes and store them securely, and use the AES encryption feature to ensure their sensitive data remains private. The app's user-friendly interface and robust features make it an ideal solution for managing passwords and sensitive information securely.
Boards Requirement 4
Create a policy or procedure that addresses events such as: a disaster recovery plan, a business continuity plan, an incident response policy, an acceptable usage document, an information security policy, a physical security policy, assessments or troubleshooting procedures.
DigiKnight Technologies BCDR
This document provides a comprehensive disaster recovery plan for a company, including information on departments, facility description, procedures, emergency contacts, backup deployment, action plans, risk assessment, and service contracts. The plan covers potential risks and threats, such as fires, power outages, IT and technology-based threats, environmental threats, and human-caused hazards, and outlines measures to address them, such as evacuation plans, backup policies, and security protocols.
Microsoft Active Directory Domain Services
The configuration of Microsoft Active Directory Domain Services (AD DS) for Carmour.com has been completed. Organizational Units (OUs) have been created based on regional office locations, and delegation tasks have been assigned to the Account Operators and Server Operators groups. Various objects have been created, moved, and configured within AD DS, including user accounts, group policies, shared printers, and folders. The Find feature has been used to locate users with "admin" in their usernames, and a custom password policy has been created for the IT department.
Boards Requirement 5
Develop a research report or implementation plan concerning legal and ethical best practices and mandated requirements that pertain to information security.
Principles of Information
This is a well-structured and comprehensive set of principles for information security. The principles cover a wide range of aspects of information security, including physical security, virtual security, employee training, risk management, and vulnerability disclosure. The principles emphasize the importance of confidentiality, integrity, and availability, as well as the need for a multilayer protection system and a balance between security and functionality. The principles also stress the importance of employee training and awareness, as well as the need for a risk-based approach to security. Overall, these principles provide a solid foundation for any organization looking to improve its information security posture.
Security Program Implementation Plan
This is a security program implementation plan prioritizes protecting vital client and company information through physical security measures such as COVID-19 restrictions, entrance gate implementation, and restricted access to certain areas. Access control measures include identification requirements, password policies, and network segmentation. The plan also includes protection for client information, server rooms, and network traffic through encryption, backup power, intrusion detection scanning, and firewall restriction rules.
Boards Requirement 6
Research, document, test and evaluate several current industry information security based threats, risks, malicious activities, covert methodology, encryption technologies, mitigation techniques or unconventional tactics to prevent loss of sensitive information and data confidentiality, integrity and availability.
Information Assurance Risk
This document discusses the risks and potential impact of phishing attacks, particularly the Trickbot Malware Phishing Campaign. The company's vulnerability to such attacks is highlighted, along with potential consequences such as data breaches and litigation. To mitigate the risks, the article suggests mandating social engineering training for employees, implementing password and technology policies, encrypting company and client data, and utilizing 2-factor authentication for employee logins.
National Vulnerability Database & Common Weakness Enumeration
This document focuses on the National Vulnerability Database (NVD) and Common Weakness Enumeration (CWE), which are databases of known technology-based vulnerabilities. It explains that there are over 160,000 vulnerabilities listed on the NVD, and provides an overview of the top 25 most common and impactful vulnerabilities listed on the CWE. The document recommends that businesses and consumers stay up to date on newly discovered vulnerabilities, utilize security platforms for vulnerability assessments, and keep their systems up to date to improve security.
Mock Social Engineering Attack
This document describes a social engineering phishing attack that was conducted as part of a final project for a social engineering course. The attack was done via email, using a spoofed email address from GitHub to increase the credibility of the email. The goal was to convince the target to click on a link to a fake GitHub Education Pack renewal page that was set up as a payload. The author used Microsoft Direct Send feature of Microsoft 365 subscriptions to send the email without authentication. The attack was successful in that it made it past the email spam filter and was reviewed by the target. The author received feedback on how to improve the attack and acknowledged that it was a mock attack for educational purposes only.
GTD Elk Stack Dashboard
ELK Stack dashboard using the Global Terrorism Database provided by the National Consortium for the Study of Terrorism in Response to Terrorism (START). The dashboard includes modules for filtering data, selecting countries, heat maps, attack rates over time, and graphs showing the most frequent target types, attack types, and deadliest attacks. Overall, the project is a demonstration of how ELK stack can be used for data analysis and visualization.